Tech Bytes & More
by Meadow Mountain Technology
Welcome to our Help Center. We are here to help you make mole hills out of technology mountains.
We hope you'll become fawned of our new and improved help center.
A Message From Jason...
I bet you just said oh deer, not another pun. Don’t worry, I’ll rack them up in due time. Anyway, welcome to our new and improved Tech Bytes by Meadow Mountain Technology. We plan to bring you more content on a regular basis. Myself, along with a new contributor Devynn Brant (Marketing & Content Specialist) designed this space to be a hub of knowledge. We want customers and visitors alike to find value in the information we have. Short of giving away the secret sauce behind our business, we are sharing how to’s for those of our viewers who are interested in handling their technology needs themselves, product reviews, deep dives into frequently asked questions and more.
Jason Patterson, CEO of Meadow Mountain Technology
Your Featured Resources

Optimizing Your Wi-Fi Network for Better Performance
To optimize your Wi-Fi performance and ensure a fast and reliable internet connection, consider following these best practices: Position your router strategically: Place your router
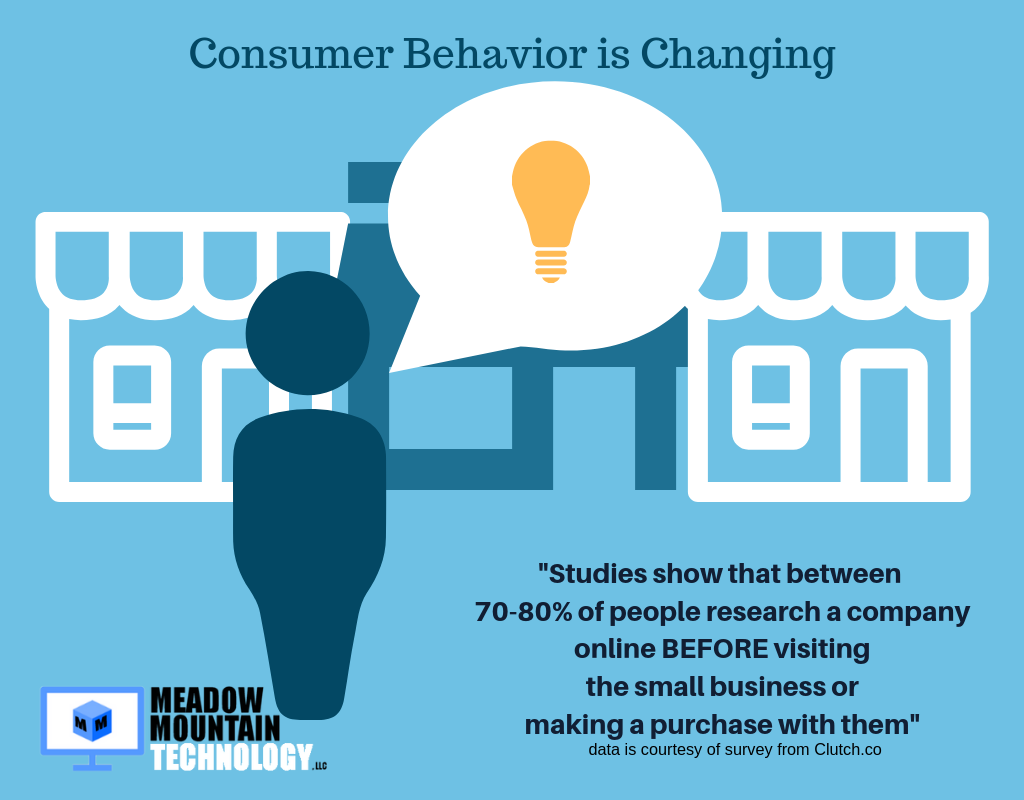
Does My Small Business Need A Website?
Four Reasons A Small Business Needs a Website Small businesses face obstacles that restrict their online presence. Some of these obstacles are created by misguided

Meadow Mountain Refocus: Getting our Blog Back on Track
Back to the Grind Hi readers, We’ve been a little sloppy with the blog since starting it. Like really sloppy. We made first time blogger
Subscribe to Our Blog

New App Aims to Break the Stigma on Mental Illness
New App iRel8 Aims to Break the Stigma Surrounding Mental Illness This is a different direction than my usual cyber security and tech tips blog

The Latest on the Meltdown and Spectre Vulnerabilities
The Latest on the Meltdown and Spectre Vulnerabilities Researchers are getting closer to a turning Meltdown into a useful attack The Meltdown and Spectre vulnerabilities

Making Sense of the Meltdown and Spectre Vulnerabilities
Making Sense of the Meltdown and Spectre Vulnerabilities I’m sure by now many of you have heard the words Meltdown and Spectre. No Meltdown isn’t

The Anatomy of a Strong Password
The Anatomy of a Strong Password According to many reports out there, the Equifax security breach was caused by installing a piece of software and

Cyber Security and Small Business
Cyber Security and Small Business Best practices for keeping your small business information secure. We’ve all heard the stories on the news about hackers and

What’s Dragging You Down, Computer?
What’s Dragging You Down, Computer? Simple tips to speed up your slow PC… All we want to do is turn on our PC to check
Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
